Just yesterday, the notable social media platform Twitter and a number of its high-profile users fell victim to a flashy Bitcoin scam.
Let’s take a look at what happened during this news breaking hoax and see what Kevin Mitnick, once coined The World’s Most Famous Hacker, has to say about the breach and cryptocurrency con.
What Happened?
On Wednesday July 16, 2020, many prominent, highly-followed Twitter users simultaneously posted “double your Bitcoin” Tweets. These social posts told their followers that if they contributed money by clicking a link, the figure would match the donation, returning double the amount back.
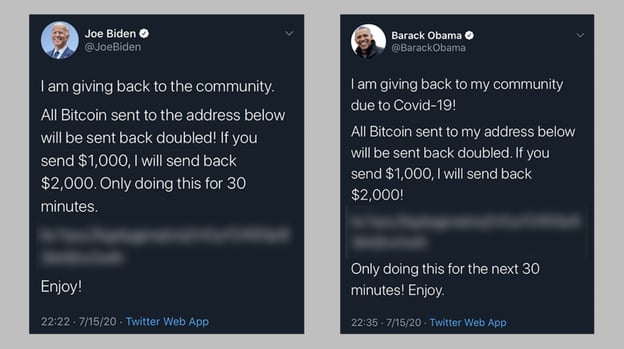
Well-respected leaders like former U.S. President Barack Obama and current Democratic presidential candidate Joe Biden were amongst some of the political accounts hacked. Celebrities like Elon Musk and media billionaire Mike Bloomberg were also targeted, as well as big brands like the tech creators Apple and the ride-sharing app Uber.
Because the posts were published near simultaneously, news of the breach spread quickly. Many brands took down the malicious Tweets and locked their social media accounts within minutes of the incident.
For many, however, damage was already done. The accounts targeted had millions of followers and within minutes received hundreds of contributions, reportedly totalling over $100K in Bitcoin as of Thursday morning, according to The BBC.
Here's a recap of the scenario from Kevin via CNN:
How the Hackers Got In
How could this happen? How did hackers gain full access to login credentials of these notable, “verified” Twitter users all at once?
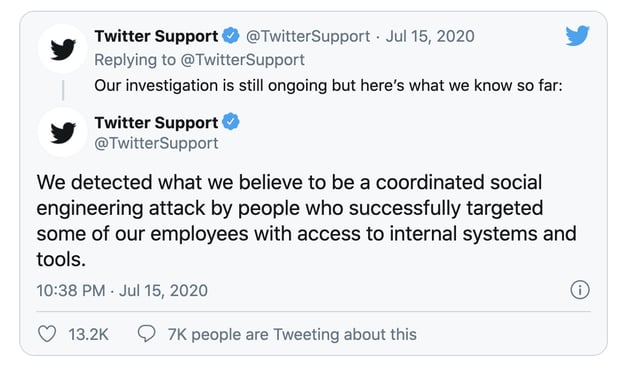
Bad actors caught the big fish: Twitter itself.
Through a series of highly-targeted social engineering attacks, hackers exploited Twitter employees to make their way through Twitter’s internal systems and gain administrative access to high-profile usernames and passwords.
It Could Have Been Worse
While the personal financial loss of those who contributed funds and implications this scam could have on brand reputation are no joking matter, cybersecurity professional, Kevin Mitnick, claims this Twitter hack could have been much worse.
In his interview with BBC World News, Kevin claims the hackers could have made significantly more money and executed a more efficient exploit had they done so more quietly.
The hackers “could have sold this access for millions of dollars, most certainly.” Mitnick said in a statement, “They were very noisy about this attack… this wasn’t stealth and clever. This was an attack to bring notice to the community.”
Reports on a suspicious Instagram account reveal the hackers may view their Twitter scam as a “charity attack” and that all money received “will find its way to the right place.” But Kevin reminds us that with the access level these bad actor’s unlocked (possibly having eyes on all the direct messages of every Twitter account compromised), they could have leveraged data to target individual users, hacking their way into major brands across the world.
“It was very noisy” Kevin comments. Because the bad actors made such a show of the affair, they missed wider opportunities to gain deep access and make substantially more money. “In the hacking community, we would actually call this type of hack a bit lame,” Kevin notes.
Key Takeaways from the Twitter Scam
Whenever a major enterprise or notable brands are hacked, there are valuable lessons to be gleaned.
Here are a few high-level takeaways for protecting your business from similar hacks:
- Routinely monitor your social media channels. Many managers realized their Twitter account was compromised within minutes of the unauthorized post going live. By taking down the malicious Tweet quickly and locking out their account, individual brands reduced the number of contributions received and severity of the breach.
- Educate your team on social engineering tactics. Twitter’s weakest link was their employees. Hackers targeted staff who had privileged access to internal systems and tools through a series of social engineering ploys. Discover a few of the ways bad actor’s use social engineering to trick you and your team and invest in professional security training to empower your employees to think before they click.
- Acknowledge you aren’t impervious to cyberthreats. None of these brands, outside of Twitter itself, did anything wrong. Even with strong passwords, the hack was beyond their control. Hackers went after the big dog and got the keys to the Tweet Kingdom. By maintaining a mindset that you’re never completely hack-proof, you can keep your guard up and better prepare for the unpredictable.
Social Engineering Strength Testing
Do you know how you and your employees would stand up against clever social engineering exploits?
At Mitnick Security, we conduct simulated cyber attacks on your company, targeting unknowing employees and management to test if they’ll fall victim to our tricks. After our experiment, you’ll gain insight into tangible ways to improve your defenses— straight from one of the highest-respected teams in the cyber security business.
Learn more about our social engineering strength testing services here.



