Experts across a myriad of industries will defend the value of performing a routine penetration test, but not all pentests are created equal.
A pentest is really only as valuable as the detail and comprehensiveness of its report, for those who receive it to understand how to best apply the results.
While there are six types of penetration tests, each report should have a similar structure— following the four phases of penetration testing— regardless of who performed it.
In our previous post, What’s Included in a Pentest Report, we took a high-level look at what you could expect to receive post-attack. In this deeper dive into the anatomy of a pentest, we’ll break down what you can typically expect from your final report.

An Executive Summary
An executive summary is exactly what it sounds like: a summary of the report's findings, intended for the company’s executives.
This abbreviated version of the full report is aimed at providing actionable takeaways for the C-suite, in an easily understandable language without the technical detail. Because of its concise, direct nature, most pentest reports begin with this high-level overview.
Here are a few things you can expect a pentesting report’s executive summary to include:
Positive Observations
Some pentesters like to start off with a few examples of where the company is excelling in their security measures. Since the majority of the report heavily focuses on ways the subject’s security is failing, this beginning section can help to remind readers that at least part of their defenses and efforts are worthy of recognition.
Examples of Positive Observations
- When (a certain employee) got alerted of (specific security attempt), he reported the suspicious activity to IT
- (Specific employee or group of employees) didn’t have passwords cached in their browser, making it harder for the pentesters to find a pathway in
Attacker Objectives Accomplished
Right from the start, the pentester will detail what they were able to do once they compromised the target’s infrastructure. This is typically compiled into a bulleted list, revealing a summary of achievements the pentester accomplished.
Examples of Objectives Accomplished
- Extracted all (email provider) user password hashes on the domain
- Compromised (server name or endpoint)
- Obtained access to a predefined target (i.e. intellectual property, source code, financial information, client list, etc.) or obtained access to a previously unidentified target uncovered during the process
Strategic Recommendations
After the pentesters outline where they gained access, they’ll dive into their recommendations for mitigating, transferring, or accepting your risks.
It’s here that they’ll break down clearly segmented short-term, medium-term, and long-term goals.
Examples of Goal Buckets
These different buckets will vary based on your pentester, but they should clearly define the parameters of each goal type within their unique scoring system.
Here’s how we segment goals at Mitnick Security:
- Short-term goals are advised to be completed three months post-test
- Medium-term goals tackled within six months
- Long-term goals within the next two years
Your strategic recommendations will be highly customized to your unique business issues, but for the sake of an example, here are a few common bullets you might see in a sample pentesting report:
Examples of Recommendations
- Set a password policy of minimum 25 characters without enforcing case, numbers, or symbols
- Enable multi-factor authentication on external-facing login interfaces and where multi-factor authentication is supported, ensure that it is enforced for everyone
- Configure password manager applications to log out after 15 minutes of idle time
In the example above, all recommendations relate to password management, but a real pentesting report would offer an array of advice, covering the full picture of the target’s security issues.
When looking at a sample pentesting report, look for actionable, helpful recommendations. Advice like “improve password management” is too broad and unspecific.
On the other side of the coin, be wary of pentesters who are overly specific. The Mitnick Security team is product agnostic, meaning we rarely recommend specific software/products as solutions: technology is always changing and business needs are never the same from industry-to-industry. Instead, we offer suggestions for what you need to do. From there, it’s the internal security team’s choice on who or what they use to achieve the outlined security goals.
Custom Features
Companies with specific or unique goals may require their own customization inside the traditional pentesting report template. For instance, if you were looking to delve deeper into your risk threshold, your report may include a subsection on Risk Rating & Comparison within your industry.
If there’s an important element you want analyzed or explored by the security team, make sure you choose a partner willing to deliver on your expectations.
Objective & Scope
Once the report begins a detailed discussion of the objective and scope, this is often a clear indicator of where the Executive Summary portion ends. The following sections of a pentesting report are meant for IT professionals and those within/outside of the company responsible for making the strategic recommendations. It’s here you’ll see clearly defined objectives, those that the testers and target agreed upon pre-test.
Example Objective & Scope
- Perform an external network penetration test on (client’s) (specific infrastructure).
- Perform network infiltration to determine the effectiveness of perimeter security controls and to assess detection capabilities.
- Provide a comprehensive report detailing any identified vulnerabilities with recommendations to remediate any identified security shortcomings.
This section is critical for those who weren’t privy to the intent from the beginning, allowing them to understand the main goals of the test. It’s here too you may see an ironed out timeline, for instance, containing the pentest to a 6-week period with specifically defined dates.
Chronological Narrative
Next, you’ll see a detailed explanation of the individual attack vectors the pentesters took to meet their objectives.
You’ll find that this section is often consistent in that it’ll detail how the pentesters plot and take an initial foothold, escalate access, and make lateral movements throughout your infrastructure until achieving their intended access.
But while the structure and attack vectors are often similar, this portion of the penetration testing report is very specific to the client, outlining step-by-step how the pentesters got into their exact systems. In this way, every narrative will be unique, often showcasing specific screenshots and examples of the attack vectors and resulting escalations.
The narrative will break down each attack method, explaining exactly what the pentester did and how they were able to manipulate users and technology to compromise your security.
The level of detail and explanation, however, will depend largely on the pentesting company you choose. Here at Mitnick Security, we differ from other pentesting reports in our unique storytelling recount. Unlike other pentesters who only display a table with findings, we distinctly outline a step-by-step explanation of how we began our test, listing specific methods in a play-by-play fashion, often with pictures and visuals, to tell the full story of how we gained access.
Phishing & Social Engineering
Phishing and social engineering often play such a significant role in any penetration test that, oftentimes, pentests give the report its own section to outline social engineering-specific attack vectors.
This section will often reveal the names and email addresses of employees targeted, with exact screenshots of phishing emails sent, timelines for how long the exploit took to unfold, and more.
Technical Vulnerabilities
After explaining the details of each attack vector, the pentesting report will approach a full list of recommendations for each vulnerability in order of criticality.
Just like every pentester will have their own recommended goal threshold in the Executive Summary, the pentester will define their unique vulnerability rating system. Typically, you can expect to see five different buckets of risk:
- Critical risk
- High risk
- Medium risk
- Low risk
- Informational (no risk)
Example Risk Rating System
Here’s an example of our risk rating system at Mitnick Security:
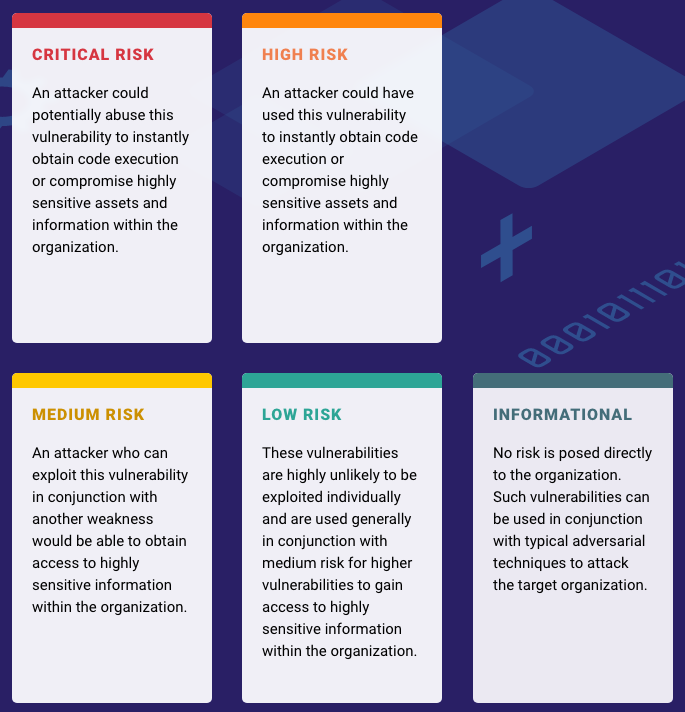
Example of a Remedial Actions Chart
From there, you will often find recommended remedial action items for each vulnerability. This is often organized into a chart that may look something like this:
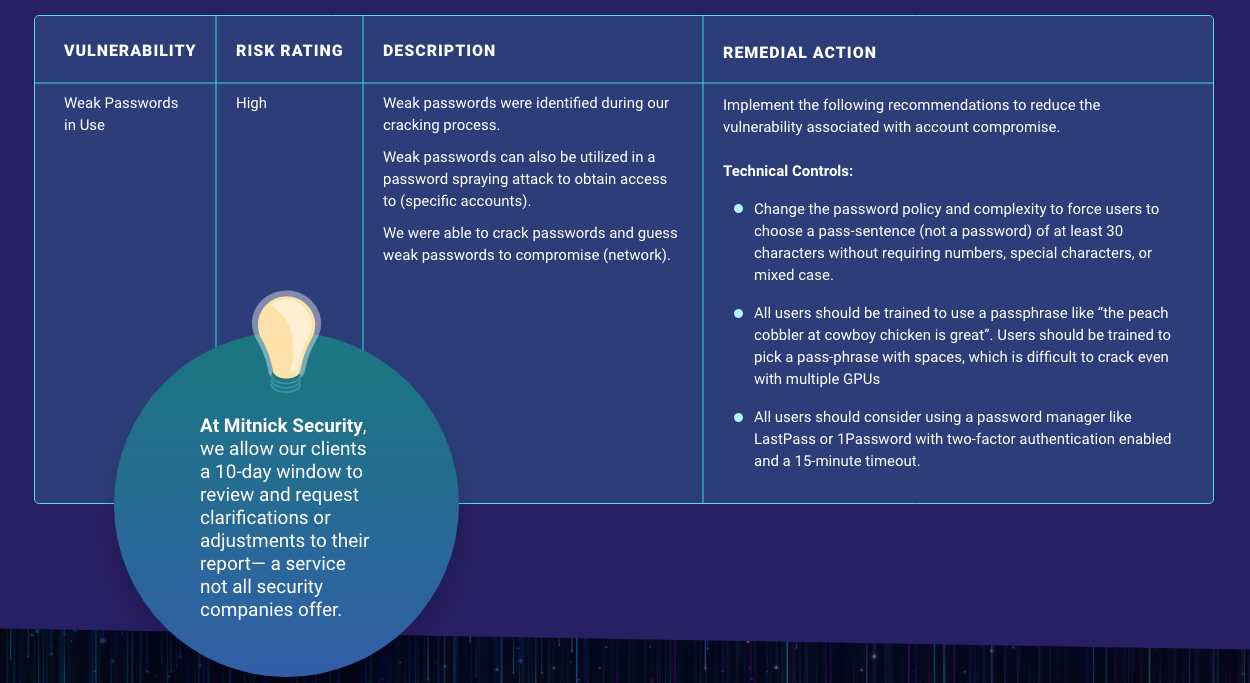
With that, your penetration testing report is complete.
Here at Mitnick Security, we allow our clients a 10-day window to review and request clarifications or adjustments to their report— a service not all penetesters offer.
What to Look for in a Pentesting Partner
Now that you understand what to expect from a well-rounded penetration testing report, it’s time to begin your search for the right partner.
When deciding on a pentester, look for a company that customizes their approach based on your organization’s unique needs— who won’t leave you with vague and unhelpful cookie-cutter reporting.
Here are four considerations before choosing the right pentesting partner to help you select the best fit for your goals.
Curious as to how a penetration testing report could transform your security? See how our team at Mitnick Security helped a client uncover critical vulnerabilities and make dramatic changes to improve their defenses.


